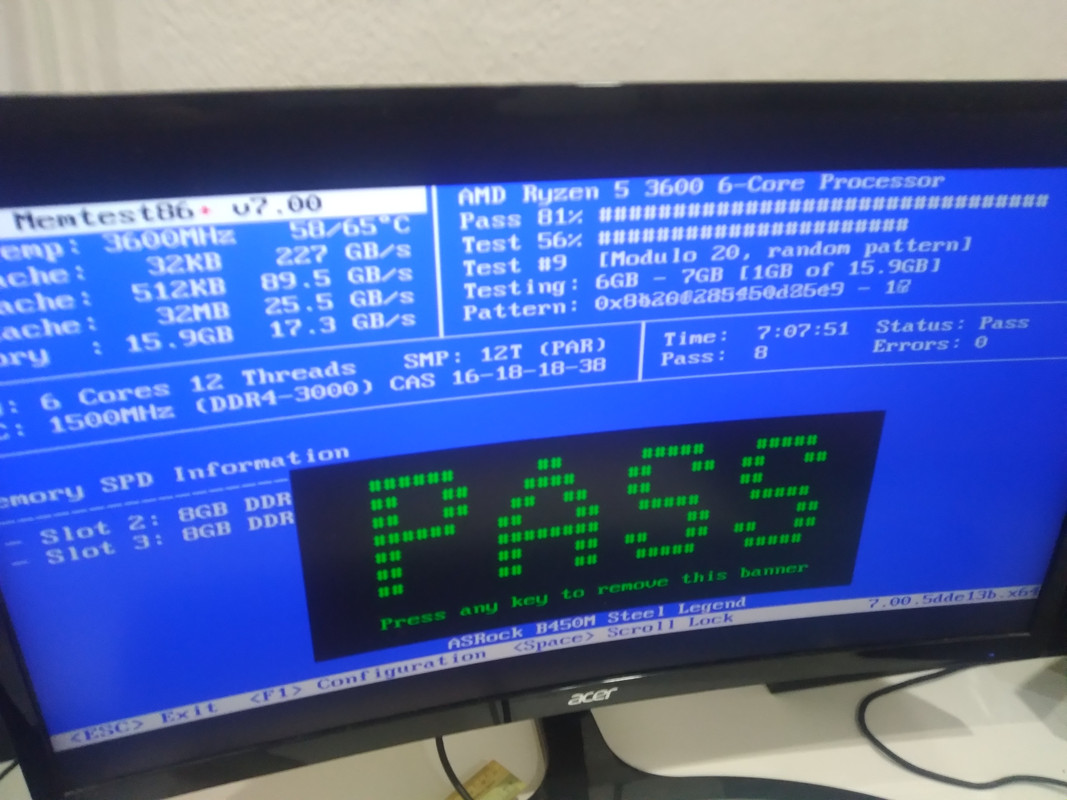
Hi, currently my build is having some kind of random BSoDs and reboots, and sometimes my machine will locks up with stuttering sound.
Some information:
Some information:
- A brief description of your problem
- System reboots and BSoDs at random, KMODE_EXCEPTION_NOT_HANDLED
- Tried reinstalling AMD chipset drivers, but to no avail
- System Manufacturer?
- Self built
- Laptop or Desktop?
- Desktop
- Exact model number (if laptop, check label on bottom)
- Self built
- OS ? (Windows 11, 10, 8.1, 8, 7, Vista)
- Windows 10
- x86 (32bit) or x64 (64bit)?
- 64 bit
- (Only for Vista, Windows 7) Service pack?
- N/A
- What was original installed OS on system?
- Windows 10
- Is the OS an OEM version (came pre-installed on system) or full retail version (YOU purchased it from retailer)?
- Retail
- Age of system? (hardware)
- 4 years+
- Age of OS installation?
- 4 years +
- Have you re-installed the OS?
- No
- CPU
- Ryzen 5 3600
- RAM (brand, EXACT model, what slots are you using?)
- 2x8GB G Skill Ripjaws V 3000CL16 (slot 2 and 3, F4-3000C16-8GVRB)
- Video Card
- Sapphire RX 5700 XT Pulse
- MotherBoard - (if NOT a laptop)
- ASRock B450M Steel Legend
- Power Supply - brand & wattage (if laptop, skip this one)
- Seasonic G-550 80+ Gold
- Is driver verifierenabled or disabled?
- No
- What security software are you using? (Firewall, antivirus, antimalware, antispyware, and so forth)
- Nothing, except Windows Defender
- Are you using proxy, vpn, ipfilters or similar software?
- No
- Are you using Disk Image tools? (like daemon tools, alcohol 52% or 120%, virtual CloneDrive, roxio software)
- No
- Are you currently under/overclocking? Are there overclocking software installed on your system?
- Yes, XMP